ANDROIDOS_GINGEROOT.A
GingerBreak
Android OS 2.3


Threat Type: Cracking Application
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This malicious application GingerBreak targets the Android platform and exploits a vulnerability presented on Android OS version 2.3 (code name: Gingerbread). After the exploit, the device is "rooted", which allows any application to acquire privilege access to any sensitive information on the device.
It also provides an option to unroot the device.
This cracking application may be manually installed by a user.
TECHNICAL DETAILS
Arrival Details
This cracking application may be manually installed by a user.
Rootkit Capabilities
This cracking application is used by other malware for its rootkit functionalities.
NOTES:
This malicious application GingerBreak targets the Android platform and exploits a vulnerability presented on Android OS version 2.3 (code name: Gingerbread). After the exploit, the device is "rooted", which allows any application to acquire privilege access to any sensitive information on the device.
It also provides an option to unroot the device.
It contains three files with the ".png" extension.
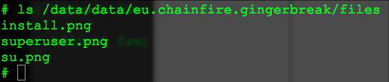
These .png files seem like ordinary image files, but actually they can really be run. su.pngis actually an executable file which elevates the current user to the superuser, as can be found in most Unix/Linux systems; superuser.png is actually an APK file, which promotes user for permission upon su is invoked; and install.png is a shell script file which installs su and superuser.apk.
Upon execution, it will change the above three files into the original filetype, and add executable permissions to them.
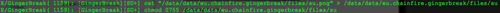 |
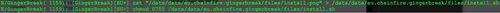 |
 |
When the main activity runs, it will run a binary named gingerbreak which does the actual job to exploit the system in the background:
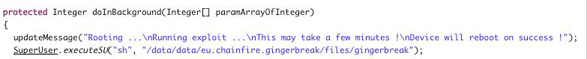
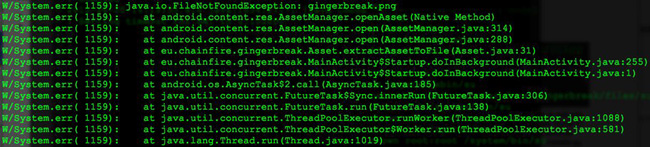
From the decompiled code, the binary named gingerbreak also comes from a faked png file named gingerbreak.png, the same trick as the three png files we mentioned above. However in this sample, the gingerbreak.png is missing in the package. This is also proved from the runtime debug log, showing that FileNotFoundException happens when it's trying to copy gingerbreak.png into gingerbreak. Maybe this sample was repacked, during which time something went wrong, and as a result, it won't actually root the device successfully.
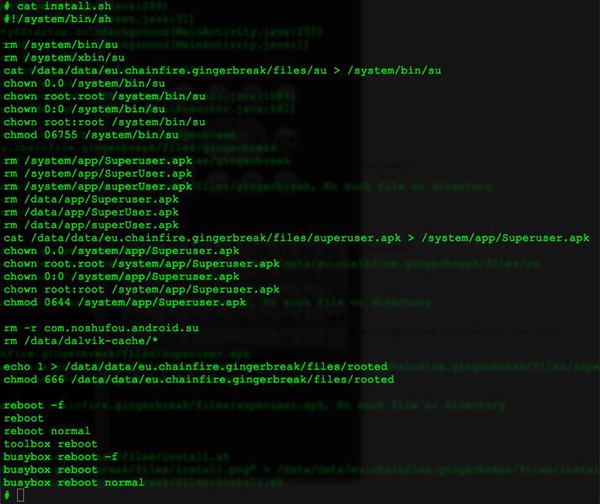
The system partition which contains system applications and important system files is by default mounted as read-only. After the exploit, the application gains unrestricted access to the device. Here it remounts the system partition into writable, so it can later write files permanently into the file system, which survive device restarts.

Then it invokes the install.sh shell script, which copies the binary su into /system/bin, and copies superuser.apk into /system/app/, where pre-installed system applications resident. These two files will provide root access to any application running on this device.
SOLUTION
Step 1
Scan your computer with your Trend Micro product to delete files detected as ANDROIDOS_GINGEROOT.A . If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Step 2
Remove unwanted apps on your Android mobile device
Did this description help? Tell us how we did.



